Digital Credentials
Multipurpose digital credentials for a composable, mobile, and verifiable world.
Digital Credentials & Wallets
Empowering secure and interoperable credential ecosystems
Digital credentials and mobile wallets are reshaping how individuals and organizations interact in the digital world. This area focuses on the design, issuance, and verification of credentials that can be used across multiple domains—maintaining security, privacy, and compliance with international standards.
The approach supports both traditional and emerging credential models, facilitating gradual adoption and coexistence between different technologies.

Credential Building Blocks
Foundations for a trusted, mobile-ready ecosystem
The framework integrates credential issuance, management, and verification into a cohesive model. Interoperability is achieved through open standards and shared trust anchors, ensuring continuity across digital ecosystems.
Credential Management
End-to-end lifecycle of credentials for individuals and organizations.
Mobile ID & Wallet
Applications that store and present identity and attribute credentials securely.
Interoperable Standards
Alignment with formats such as X.509v3, FIPS, ICAO, ISO, IETF, W3C.
Verification Gateways
Validation through APIs, trust lists, or cryptographic proofs—online or offline.

ISSUER
Establishing trust at the source
Credential issuance begins when an authorized entity, such as an identity authority or service provider, creates and signs a credential that represents verified information.
The process follows rigorous identity proofing and binding methods to ensure authenticity.
Support for multiple credential types (X.509, FIPS PIV, ISO mDL/mDOC, IETF SD-JWT, and W3C Verifiable Credentials) allows gradual migration between standards while preserving continuity of trust.
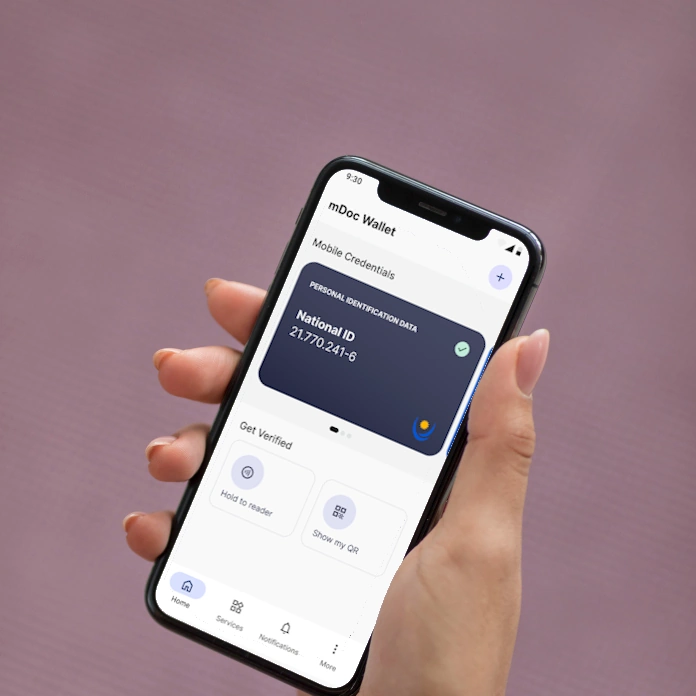
HOLDER
Empowering individuals and organizations with control
The holder manages and presents credentials through secure mobile or desktop wallets.
These applications store credentials locally, protected by device-level security and user consent mechanisms.
The holder determines when and what data to share, aligning with privacy-by-design principles and enabling selective disclosure across both online and offline interactions.

VERIFIER
Ensuring authenticity and integrity of shared data
Verifiers confirm the validity of credentials presented by holders through cryptographic proofs, trust lists, and revocation checks.
This validation can occur in real time or offline, depending on the credential type and assurance requirements.
Standardized protocols such as OIDC4VP and SD-JWT ensure interoperability and policy enforcement across systems and jurisdictions.
TRUST ANCHORS
Interoperability through governance
A trust backbone connects issuers, holders, and verifiers under a common governance model.
It establishes policies for credential assurance, key management, and interoperability, supported by registries or Trust Lists.
This model aligns with the principles of the European EUDI Wallet and NIST Digital Identity Frameworks—promoting sovereign yet interoperable ecosystems where verification remains secure, transparent, and scalable.
Multipurpose and Interoperable
Credentials beyond identification
Digital credentials extend beyond personal identity to represent qualifications, licenses, and authorizations.
By combining identity, authentication, and digital signing capabilities, organizations can enable reliable interactions and verifiable data exchange.
The coexistence of multiple credential “flavors” allows for flexibility and scalability as standards evolve, supporting both government and enterprise use cases.
Identity Credentials
Identification and Personal Data in device-based credentials.
Attribute Attestations
Digital proofs for verified attributes, information, and entitlements.
Wallet Interoperability
Support for multiple credential formats within one managed application.
Remote and Offline Verification
Cryptographically verifiable credentials with or without connectivity.
LET’S TALK
Ready to explore the future of digital credentials?
Discover how a modular and standards-based approach can enable interoperable credential ecosystems.